Secure Your Business for the Quantum Age
Post-quantum cryptography Prepare Today Be Protected Tomorrow
The Quantum Revolution Is No Longer the Future – It's Happening Now
With advancements from tech giants like Google and IBM, quantum computing is reshaping what’s technologically possible. But this progress comes with an urgent challenge: securing our digital world.
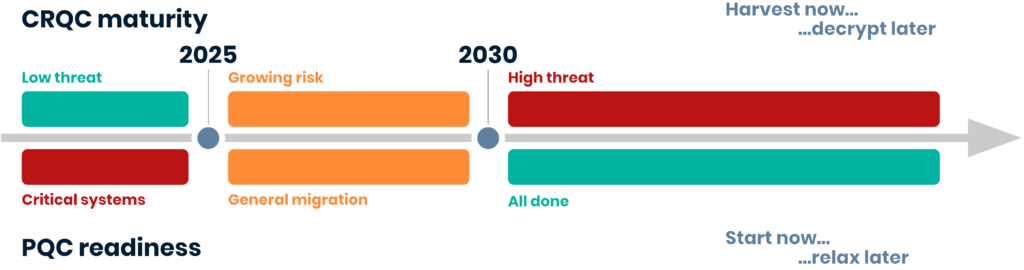
Sensitive data encrypted today may be harvested by adversaries and decrypted in the future—once quantum computers mature—a tactic known as “store now, decrypt later"
Governments, financial institutions, healthcare systems, and critical infrastructure are top targets for quantum-era attackers.
The cost of recovering from a breach may far exceed the investment in proactively deploying quantum-safe measures.
By 2030, traditional cryptographic methods may be obsolete due to the power of quantum computing.
Quantum-Safe Security Starts Here
Is the key to protecting your organization from quantum-enabled threats. It provides algorithms specifically designed to resist quantum attacks.
Also supports a hybrid approach—combining classical and post-quantum cryptography for comprehensive protection.
Secure sensitive data now and eliminate future vulnerabilities.
Stay ahead of evolving standards and strengthen customer trust.
Early adoption signals your commitment to security and innovation.
Time Is Running Out – Begin Your Transition to PQC today
Steps Toward Future-Proof Security
Technical analysis of current infrastructure and tailored recommendations.
Identify current cryptographic methods and their usage in your systems.
Enable systems to adapt flexibly to new security requirements.
Determine whether to pursue direct replacement or hybrid implementation—system by system.
Identify critical systems and the highest-risk areas.
A detailed playbook for transitioning to PQC with minimal operational disruption.
Implement quantum-safe solutions incrementally, case by case.
Why Choose Monet+ as Your Partner?
We’re a trusted market leader in secure digital identity and digital payments. Our expertise guides you through the complex shift to post-quantum cryptography.
Across financial, public, and enterprise sectors.
Committed to the success of your project.
Revenue in 2023
Where we deliver active projects

Anežka Pejlová Security Architect
Secure your organization’s future with Monet+. Contact our expert and begin your transition into the post-quantum era.